There is a lot of talk in consulting circles about the need for IT services providers to move beyond being excellent technicians and become trusted advisors.
So what does this mean in practise?
Business owners of companies with under 200 staff do not have access/budget to have an IT Director. However, by employing the services of a virtual IT director who acts as a Trusted Advisor the business owner can receive timely and appropriate advice for their business situation.
In this context, the virtual IT director will meet formally with the business owner on a regular basis to discuss strategy concerning technology platform and direction. The major benefit of this is that the business owner thus does not need to be IT-literate to make informed decisions about how to use IT to the best advantage in the business.
The alternative – and usual route for so many business owners – is to rely on one-off consultants and vendors who have the obvious agenda of wanting to push and sell their own products/services.
So what’s special about a Trusted Advisor?
Jason Haddock in his excellent blog “What does it mean to be a trusted advisor?” makes the excellent point that what lies at the heart of building a trusted relationship is TRUST!
In Mick Cope’s book, “The Seven C’s of Consulting” he outlines a great acronym for trust:
- Truthful
- Responsive
- Uniform
- Safe
- Technically Competent
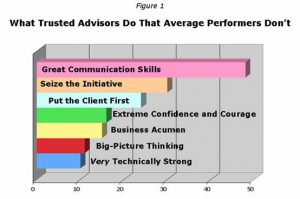
According to a recent survey: first and foremost they are great communicators – “they communicate the invisible well”. They must also display superior creativity in “listening to client issues and creating a solution strategy that clearly shows how it solves the problem quickly and thoroughly”.
Another key quality is the ability to seize the initiative, Trusted Advisors “take ownership of the client more, whereas average performers take ownership of the problem”.
What Separates Trusted Advisors from Everybody Else?
What Does a Trusted Advisor Look Like?
- Clients ask for them by name
- They are sought out for advice that goes beyond their described expertise.
- They maintain relationships that aren’t just technical.
- They have such strong personal brands that outsiders seek them out for speaking engagements, writing articles, or special projects.
Read the full report: What Trusted Advisors Do That Others Don’t
How Can PASR Help You As A Business Owner?
Peter Rigbye is the Managing Director of PASR and acts as a Virtual IT Director for many of PASR’s clients. Peter says:
“With 38 years in the IT industry, from supply, to service management, to service consumption, and with the prior 14 years in a banking environment, I am well aware of the issues that businesses face in operating, securing and protecting their IT assets. Specifically:
I diagnose your root causes rather than just fixing the problems as reported!
I specialise in solving IT issues for SME business owners… once and for all!”
If you would like to discuss this, PASR Technologies has been providing SME business owners with a level of service and support to the SME business owner that is typically only directly available in very large organisations.
Servicing businesses from 10 to up to 200 employees, our clients range from local SMEs through to regional offices of larger MNCs, and include airlines.
At PASR Technologies, we solve your IT problems before you even realize you have one!