Cyber crime has been in the news recently. A few months ago the UK press was awash with the lurid headlines of UK telco TalkTalk’s admission that it was the victim of a “significant and sustained” cyber-attack that has led to 157,000 customers’ personal details being accessed.
The UK Institute of Directors (IoD) said only “serious breaches” made the headlines, but attacks on British businesses “happen constantly”. The UK government said it was “committed to tackling cyber-crime”.
Here in Singapore we are not immune from this
Small and medium-sized enterprises (SMEs) are increasingly becoming soft targets for cyber criminals…who are increasing hacking into smaller businesses as a way of getting access to larger companies to which SMEs are suppliers.
SMEs are easy targets as often they lack the resources, expertise and technical manpower to defend themselves against cyber attacks. The situation is serious as the 2015 Internet Security Report shows that 60 per cent of all cyber attacks are on SMEs.
Ascendas’ www.spacetobe.com.sg website was hacked in 2014 – an activity that has occurred all too frequently to SG websites in past months. A concerned colleague – after being advised (three days later!) that the website’s database of personal information might have been exposed – asked me:
This is scary – so how can I be safe?
And what a good question!
Basically, we cannot. In the same way that we can protect our own homes with locks – without being a locksmith – we simply cannot guarantee that our homes will not be broken into by thieves, and precious contents stolen. Yes, we can report the matter after that fact, but as for cybercrime, we may never know what has been taken, and may not get it back.
In the mentioned case the hackers defaced the site by posting a public notice stating it had been hacked, so users, and the site owners, knew that it had occurred, but consider this more scary scenario: – if the hackers above had sufficient access to deface the site:
- How long have they had these permissions?
- Have they previously extracted out personal/private data?
- What if they just took data and did not advertise their presence this time?
A few pointers to feel safe and secure
How should we go about protecting personal information that we provide to various online resources? In the same manner that we choose good and strong locks for our doors and windows, we need to be sure that we each do the same with our online credentials, and we also need to ask the owners and managers of such resources about what security practices they follow. So there are two components here, but only one of them is under our own control.
Here’s a few pointers as to what we each must do.
- Use strong passwords. Preferably use a phrase or something easily remembered. For example, change ‘My dog’s name is Spot’ into a password MdniS. Add perhaps the year we got our dog, and a special character, and you have MdniS2011# – a very strong password that we can easily remember without writing it down.
- Use different passwords for each online resource that stores your information. If we access a lot of sites that need logins but do not store private/personal information, it’s OK to have a common username & password, but for those that do store such data, DO NOT SHARE.
- Limit the amount of information that we provide. Just because a website asks for 25 pieces of data does not mean they are all mandatory. Limit the input to only those mandatory fields necessary to use the site.
- If entering financial data like credit card numbers, make sure the site is using an encrypted connection: – look for the https
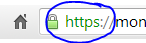 at the start of the url.
at the start of the url.
How can I be sure the site is secure?
All of the above however does not help us if the site is not secure, and this means we need to be sure that both the site owners practice good security, and the site hosters also practice good security – an entity we as site users do not have any direct contact with, which means we have to rely on the site owners. Here’s some questions you might like to ask of those that ask for your personal data.

- How do you protect my data?
- How do you protect your servers from hacking?
- How are your servers physically protected?
- Do you know who has administrative access to your servers?
- What are your policies and practices regarding password management?
- What are you policies and practices regarding terminating access for resigning employees?
- Do you change access passwords when staff leave?
- Do you disable user accounts when staff leave?
- Do all administrative users for your site share the same username and password?
- Is there an online policy available regarding security and data protection?
- Do they regularly check security logs for improper access?
- Do they have any intrusion detection/prevention systems in place?
Be aware of the risks and manage your own online information
Obviously, some of the providers we deal with may never answer these questions, and there is not a lot we as individuals can do to force them to do so – other than simply not giving them anything personal or private – but this approach will generally thwart our business, and so is not acceptable. In the end, we need to ensure that we personally manage our own online information as securely as we can, and be constantly vigilant over the bits we have no direct control over.
I personally use a lot of online resources, and supply credit card details at least weekly for purchases. Am I concerned? Sure, but simply being a luddite and stopping using them is not an option in today’s connected world. Have I ever been hacked? No, well not that I know of, but then I practice all the points I mention above, and ensure that the organisations I deal with online are reputable.
Finally, we must each remain continually aware of the risks associated with the online world, and be personally responsible for our own access.
If you would like to discuss these issues and what it means for your business, please get in touch. Since inception in 1996, PASR Technologies has been providing SME business owners with a level of service and support to the SME business owner that is typically only directly available in very large organisations.
Servicing businesses from 10 to up to 200 employees, our clients range from local SMEs through to regional offices of larger MNCs, and include airlines.
At PASR Technologies, we solve your IT problems before you even realize you have one!







